Abstract
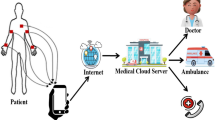
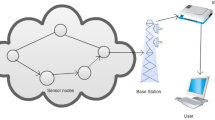
Wireless medical sensor networks (WMSN) comprise of distributed sensors, which can sense human physiological signs and monitor the health condition of the patient. It is observed that providing privacy to the patient’s data is an important issue and can be challenging. The information passing is done via the public channel in WMSN. Thus, the patient, sensitive information can be obtained by eavesdropping or by unauthorized use of handheld devices which the health professionals use in monitoring the patient. Therefore, there is an essential need of restricting the unauthorized access to the patient’s medical information. Hence, the efficient authentication scheme for the healthcare applications is needed to preserve the privacy of the patients’ vital signs. To ensure secure and authorized communication in WMSN, we design a symmetric key based authentication protocol for WMSN environment. The proposed protocol uses only computationally efficient operations to achieve lightweight attribute. We analyze the security of the proposed protocol. We use a formal security proof algorithm to show the scheme security against known attacks. We also use the Automated Validation of Internet Security Protocols and Applications (AVISPA) simulator to show protocol secure against man-in-the-middle attack and replay attack. Additionally, we adopt an informal analysis to discuss the key attributes of the proposed scheme. From the formal proof of security, we can see that an attacker has a negligible probability of breaking the protocol security. AVISPA simulator also demonstrates the proposed scheme security against active attacks, namely, man-in-the-middle attack and replay attack. Additionally, through the comparison of computational efficiency and security attributes with several recent results, proposed scheme seems to be battered.



Similar content being viewed by others
References
Khan, M. K., Chaturvedi, A., Mishra, D., and Kumari, S., On the security enhancement of integrated electronic patient records information systems. Comput. Sci. Inf. Syst. 12(2):857–872, 2015.
Istepanian, R. S., Jovanov, E., and Zhang, Y., Guest editorial introduction to the special section on m-health: Beyond seamless mobility and global wireless health-care connectivity. IEEE Trans. Inf. Technol. Biomed. 8(4): 405–414, 2004.
Wood, A., Virone, G., Doan, T., Cao, Q., Selavo, L., Wu, Y., Fang, L., He, Z., Lin, S., Stankovic, J.: Alarm-net: Wireless sensor networks for assisted-living and residential monitoring. University of Virginia Computer Science Department Technical Report 2 (2006)
Lorincz, K., Malan, D. J., Fulford-Jones, T. R., Nawoj, A., Clavel, A., Shnayder, V., Mainland, G., Welsh, M., Moulton, S., Sensor networks for emergency response: Challenges and opportunities. IEEE Pervasive Comput. 3(4):16–23, 2004.
Chen, B. R., Peterson, G., Mainland, G., and Welsh, M., Livenet: Using passive monitoring to reconstruct sensor network dynamics. Distributed Computing in Sensor Systems, pp. 79–98. Springer (2008)
van Halteren, A., Bults, R., Wac, K., Konstantas, D., Widya, I., Dokovski, N., Koprinkov, G., Jones, V., Herzog, R.: Mobile patient monitoring: The mobihealth system (2004)
Fischer, M., Lim, Y. Y., Lawrence, E., and Ganguli, L. K., Remotecare: Health monitoring with streaming video. 7th International Conference on Mobile Business (ICMB’08), pp. 280–286. IEEE (2008)
Bellifemine, F., Fortino, G., Giannantonio, R., Gravina, R., Guerrieri, A., Sgroi, M., Spine: A domain-specific framework for rapid prototyping of wbsn applications. Software: Practice and Experience 41(3): 237–265, 2011.
Ng, J. W., Lo, B. P., Wells, O., Sloman, M., Peters, N., Darzi, A., Toumazou, C., Yang, G. Z.: Ubiquitous monitoring environment for wearable and implantable sensors (ubimon). International Conference on Ubiquitous Computing (Ubicomp). Citeseer (2004)
de los Angeles Cosio Leon, M., Hipolito, J. I. N., and García, J. L.: A security and privacy survey for wsn in e-health applications. Electronics, Robotics and Automotive Mechanics Conference, 2009. CERMA’09, pp. 125–130. IEEE (2009)
Ng, H., Sim, M., and Tan, C., Security issues of wireless sensor networks in healthcare applications. BT Technol. J. 24(2):138–144, 2006.
Mishra, D., Chaturvedi, A., and Mukhopadhyay, S., An improved biometric–based remote user authentication scheme for connected healthcare. Int. J. Ad Hoc Ubiquitous Comput. 18(1-2):75–84, 2015.
Alemdar, H., and Ersoy, C., Wireless sensor networks for healthcare: A survey. Comput. Netw. 54(15): 2688–2710, 2010.
Das, A. K., Sutrala, A. K., Odelu, V., and Goswami, A., A secure smartcard-based anonymous user authentication scheme for healthcare applications using wireless medical sensor networks. Wirel. Pers. Commun.,1–35, 2016.
Wazid, M., Zeadally, S., Das, A. K., and Odelu, V., Analysis of security protocols for mobile healthcare. J. Med. Syst. 40(11):229, 2016.
Mishra, D., On the security flaws in id-based password authentication schemes for telecare medical information systems. J. Med. Syst. 39(1):154, 2015.
Khan, M.K., and Kumari, S., An improved user authentication protocol for healthcare services via wireless medical sensor networks. Int. J. Distrib. Sens. Netw. 10(4):1–10, 2014.
Wu, F., Xu, L., Kumari, S., and Li, X., An improved and anonymous two-factor authentication protocol for health-care applications with wireless medical sensor networks. Multimedia Systems,1–11, 2015.
Xu, L., and Wu, F., Cryptanalysis and improvement of a user authentication scheme preserving uniqueness and anonymity for connected health care. J. Med. Syst. 39(2):1–9, 2015.
Hu, F., Jiang, M., Wagner, M., and Dong, D. C., Privacy-preserving telecardiology sensor networks: Toward a low-cost portable wireless hardware/software codesign. IEEE Trans. Inf. Technol. Biomed. 11(6):619–627, 2007.
Mishra, D., and Mukhopadhyay, S., Cryptanalysis of pairing-free identity-based authenticated key agreement protocols. International Conference on Information Systems Security, pp. 247–254. Springer (2013)
Mishra, D., Mukhopadhyay, S., Chaturvedi, A., Kumari, S., and Khan, M. K., Cryptanalysis and improvement of yan et al.s biometric-based authentication scheme for telecare medicine information systems. J. Med. Syst. 38(6):24, 2014.
Chen, H. M., Lo, J. W., and Yeh, C. K., An efficient and secure dynamic id-based authentication scheme for telecare medical information systems. J. Med. Syst. 36(6):3907–3915 , 2012.
Lin, H. Y., On the security of a dynamic id-based authentication scheme for telecare medical information systems. J. Med. Syst. 37(2):9929, 2013.
Cao, T., and Zhai, J., Improved dynamic id-based authentication scheme for telecare medical information systems. J. Med. Syst. 37(2):9912, 2013.
Xie, Q., Zhang, J., and Dong, N., Robust anonymous authentication scheme for telecare medical information systems. J. Med. Syst. 37(2):9911, 2013.
Le, X. H., Khalid, M., Sankar, R., and Lee, S., An efficient mutual authentication and access control scheme for wireless sensor networks in healthcare. J. Netw. 6(3):355–364, 2011.
Huang, H. F., Chang, Y. F., and Liu, C. H., Enhancement of two-factor user authentication in wireless sensor networks. IEEE 6th International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP), pp. 27–30 (2010)
Mishra, D., Srinivas, J., andMukhopadhyay, S., A secure and efficient chaotic map-based authenticated key agreement scheme for telecare medicine information systems. J. Med. Syst. 38(10):1–10, 2014.
Mishra, D., Das, A. K., Chaturvedi, A., and Mukhopadhyay, S., A secure password-based authentication and key agreement scheme using smart cards. J. Inf. Secur. Appl. 23:28–43, 2015.
He, D., Zeadally, S., Kumar, N., and Lee, J. H., Anonymous authentication for wireless body area networks with provable security. IEEE Syst. J.,1–12, 2016.
Li, X., Niu, J., Khan, M. K., and Liao, J., An enhanced smart card based remote user password authentication scheme. J. Netw. Comput. Appl. 36(5):1365–1371, 2013.
Xu, X., Zhu, P., Wen, Q., Jin, Z., Zhang, H., and He, L., A secure and efficient authentication and key agreement scheme based on ecc for telecare medicine information systems. J. Med. Syst. 38(1):9994, 2013.
Lee, T. F., Chang, I. P., Lin, T. H., and Wang, C. C., A secure and efficient password-based user authentication scheme using smart cards for the integrated epr information system. J. Med. Syst. 37(3):9941, 2013.
Jiang, Q., Ma, J., Lu, X., and Tian, Y., Robust chaotic map-based authentication and key agreement scheme with strong anonymity for telecare medicine information systems. J. Med. Syst. 38(2):12, 2014.
Bin Muhaya, F. T., Cryptanalysis and security enhancement of zhu’s authentication scheme for telecare medicine information system. Secur. Commun. Netw. 8(2):149–158, 2015.
Zhu, Z., An efficient authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6): 3833–3838, 2012.
Khan,M. K., and Kumari, S., An authentication scheme for secure access to healthcare services. J. Med. Syst. 37(4):9954, 2013.
Arshad, H., and Nikooghadam, M., An efficient and secure authentication and key agreement scheme for session initiation protocol using ecc. Multimedia Tools and Applications 75(1):181–197, 2016.
Mir, O., van der Weide, T., and Lee, C. C., A secure user anonymity and authentication scheme using avispa for telecare medical information systems. J. Med. Syst. 39(9):89, 2015.
Das, M. L., Two-factor user authentication in wireless sensor networks. IEEE Trans. Wireless Commun. 8 (3):1086–1090, 2009.
Chen, T. H., and Shih, W. K., A robust mutual authentication protocol for wireless sensor networks. ETRI J. 32(5):704–712, 2010.
Khan, M. K., and Alghathbar, K., Cryptanalysis and security improvements of ’two-factor user authentication in wireless sensor networks’. Sensors 10(3):2450–2459, 2010.
Kumar, P., Lee, S. G., and Lee, H. J., E-sap: Efficient-strong authentication protocol for healthcare applications using wireless medical sensor networks. Sensors 12(2):1625–1647, 2012.
He, D., Kumar, N., Chen, J., Lee, C. C., Chilamkurti, N., and Yeo, S. S., Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimedia Systems 21(1):49–60, 2013.
Li, X., Niu, J., Kumari, S., Liao, J., Liang, W., and Khan, M. K., A new authentication protocol for healthcare applications using wireless medical sensor networks with user anonymity. Secur. Commun. Netw. 9(15): 2643–2655, 2016.
Siddiqui, Z., Abdullah, A. H., Khan, M. K., and Alghamdi, A. S., Smart environment as a service: Three factor cloud based user authentication for telecare medical information system. J. Med. Syst. 38(1):9997, 2014.
Mishra, D., Mukhopadhyay, S., Kumari, S., Khan, M. K., and Chaturvedi, A., Security enhancement of a biometric based authentication scheme for telecare medicine information systems with nonce. J. Med. Syst. 38(5): 1–13, 2014.
Mir, O., and Nikooghadam, M., A secure biometrics based authentication with key agreement scheme in telemedicine networks for e-health services. Wirel. Pers. Commun. 83(4):2439–2461, 2015.
Das, A. K., Odelu, V., and Goswami, A., A secure and robust user authenticated key agreement scheme for hierarchical multi-medical server environment in tmis. J. Med. Syst. 39(9):92, 2015.
Das, A. K., A secure user anonymity-preserving three-factor remote user authentication scheme for the telecare medicine information systems. J. Med. Syst. 39(3):30, 2015.
David, D. B., Mutual authentication scheme for multimedia medical information systems. Multimedia Tools and Applications,1–19, 2016.
Amin, R., Islam, S. H., Biswas, G., Khan, M. K., Leng, L., and Kumar, N., Design of anonymity preserving three-factor authenticated key exchange protocol for wireless sensor network. Comput. Netw. 101:42–62, 2016.
Dolev, D., and Yao, A. C., On the security of public key protocols. IEEE Trans. Inf. Theory 29(2):198–208, 1983.
Messerges, T. S., Dabbish, E. A., and Sloan, R. H., Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 51(5):541–552, 2002.
Kocher, P., Jaffe, J., and Jun, B., Differential power analysis. In: Proceedings of Advances in Cryptology - CRYPTO’99, Vol. 1666, pp. 388–397. LNCS (1999)
Wu, F., Xu, L., Kumari, S., and Li, X., A new and secure authentication scheme for wireless sensor networks with formal proof. Peer-to-Peer Networking and Applications,1–15, 2015.
Mishra, D., Design and analysis of a provably secure multi-server authentication scheme. Wirel. Pers. Commun. 86(3):1095–1119, 2016.
AVISPA: Automated Validation of Internet Security Protocols and Applications http://www.avispa-project.org/. Accessed on January, Vol. 2015,
He, D., and Wang, D., Robust biometrics-based authentication scheme for multiserver environment. IEEE Syst. J. 9(3):816–823, 2015.
Odelu, V., Das, A. K., and Goswami, A., A secure biometrics-based multi-server authentication protocol using smart cards. IEEE Trans. Inf. Forensics Secur. 10(9):1953–1966, 2015.
Odelu, V., Das, A. K., and Goswami, A., An effective and robust secure remote user authenticated key agreement scheme using smart cards in wireless communication systems. Wirel. Pers. Commun. 84(4):2571–2598, 2015.
He, D., Kumar, N., Shen, H., and Lee, J. H., One-to-many authentication for access control in mobile pay-tv systems. Science China Information Sciences 59(5):052108, 2016.
Das, A. K., Sutrala, A. K., Kumari, S., Odelu, V., Wazid, M., and Li, X., An efficient multi-gateway-based three-factor user authentication and key agreement scheme in hierarchical wireless sensor networks. Secur. Commun. Netw. 9(13):2070–2092, 2016.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Disclosure of potential conflicts of interest
The authors declare that they have no conflict of interest.
Research involving human participants and/or animals
This article does not contain any studies with human participants or animals performed by any of the authors.
Informed Consent
This article does not contain any studies with human participants performed by any of the authors.
Additional information
This article is part of the Topical Collection on Mobile & Wireless Health
Rights and permissions
About this article
Cite this article
Srinivas, J., Mishra, D. & Mukhopadhyay, S. A Mutual Authentication Framework for Wireless Medical Sensor Networks. J Med Syst 41, 80 (2017). https://doi.org/10.1007/s10916-017-0720-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-017-0720-9