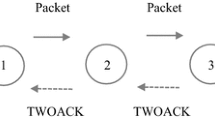
Abstract
One of the specially designated versatile networks, commonly referred to as MANET, performs on the basics that each and every one grouping in nodes totally operate in self-sorting out limits. In any case, performing in a group capacity maximizes quality and different sources. Mobile ad hoc network is a wireless infra-structureless network. Due to its unique features, various challenges are faced under MANET when the role of routing and its security comes into play. The survey has exhibited that the effect of failures during the data transmission has not been considered in the present research. The majority of techniques for specially appointed systems just decides the way and transmits the information which prompts to parcel drop in the event of disappointments, therefore bringing about low reliability. A major part of the existing research has neglected the use of the rejoining processing of the root nodes network. Most of the existing techniques are based on detecting the failures but the use of path re-routing has also been neglected in the existing methods. Here, we have proposed a method of path re-routing for managing the authorized nodes and managing the keys for group in ad hoc environment. Securing Schemes, named as 2ACK and the EGSR schemes have been proposed, which may be truly interacted to most of the routing protocol. The path re-routing has the ability to reduce the ratio of dropped packets. The comparative analysis has clearly shown that the proposed technique outperforms the available techniques in terms of various quality metrics.







Similar content being viewed by others
References
Kazemi H et al (2008) MMAN—A monitor for mobile ad hoc networks: design, implementation and experimental evaluation. The Third ACM International Workshop on Wireless Network Testbeds, Experimental Evaluation and Characterization (WiNTECH 2008)
Bandeira Duarte OCM, Fernandes NC (2009) An efficient group key management for secure routing in ad hoc networks. GTA/PEE/COPPE—Universidade Federal do Rio de Janeiro Rio de Janeiro
Perkins CE, Bhagwat P (1994) Highly dynamic destination sequenced distance–vector steering (DSDV) for mobile computers. ACM SIGCOMM Comput Commun Rev 24(4):234–244
Tsudik G, Waidnerand M, Steiner M (2000) Key agreement in dynamic peer groups. IEEE Trans Distrib Syst Parallel Syst 11(8):769–780
Clausen T, Jacquet P (2003) Optimized link state routing protocol (OLSR). RFC 3626
Tan CH, Teo JCM (2005) Energy-efficient and scalable group key agreement for large ad hoc networks. In 2nd ACM international workshop on Performance evaluation of wireless ad hoc, sensor, and ubiquitous networks (PE-WASUN’05), pp 114–121
Safavi-Naini R, Luo L, Susilo W, Baek J (2006) Self-organised group key management for ad hoc networks. In ACM Symposium on Information, computer and communications security (ASIACCS’06), pp 138–147
Chrisment I, Festor O, Bouassida MS (2006) Efficient group key management protocol in MANETs using the multipoint relaying technique. In: Intl. Conference on Networking, Intl. Conference on Mobile Communications, Intl. Conference on Systems and Learning Technologies (ICN/ICONS/MCL 2006), pp 64–71
Niu Q (2007) Study and implementation of a improved group key protocol for mobile ad hoc networks. In: 8th ACIS International Conference on artificial intelligence, parallel/distributed computing, software engineering and networking (SNPD 2007) 1:304–308
Konstantinou E (2008) Cluster-based group key agreement for wireless ad hoc networks. In: 3rd International Conference on reliability, security and availability (RESA 08), pp 550–557
Chou KY, Chen YR, Tzeng WG (2011) An efficient and secure group key management scheme supporting frequent key updates on Pay-TV systems. In: Network Operations and Management Symposium (APNOMS), 13th Asia-Pacific
Prasanna S, Balaji N, Ramya Priyadharshini M (2014) Energy and mobility based group key management in mobile ad hoc networks. Recent Trends in Information Technology (ICRTIT), 2014 International Conference
Rama Krishna C, Sharma S (2015) An efficient distributed group key management using hierarchical approach with elliptic curve cryptography. Computational Intelligence and Communication Technology (CICT), 2015 IEEE International Conference
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Singh, T., Singh, J. & Sharma, S. Re-joining of authorized nodes in MANETs using EGSR scheme and detection of internal attacks using 2ACK shceme. Int. j. inf. tecnol. 12, 295–301 (2020). https://doi.org/10.1007/s41870-018-0155-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s41870-018-0155-7