Abstract
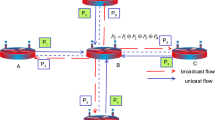
In this paper, first, we propose Star-NC, a new network coding (NC) scheme for multiple unicast sessions in an n-input n-output star structure. Then, we evaluate the network throughput of this coding scheme in wireless mesh network over the traditional non-NC transmission. Our scheme benefits from the proximity of all the nodes around the relay node and employs a more general form of overhearing different from other schemes such as COPE. We found that the gain of our NC scheme depends on both the star size and the routing pattern of the unicast transmissions. Based on this, we identify both the situations which the maximum gain is achievable and a lower bound for the expected value of the gain in the case of random routing pattern. Next, we propose an analytical framework for studying throughput gain of our Star-NC scheme in general wireless network topologies. Our theoretical formulation via linear programming provides a method for finding source-destination routes and utilizing the best choices of our NC scheme to maximize the throughput. Finally, we evaluate our model for various networks, traffic models and routing strategies over coding-oblivious routing. We also compare the throughput gain of our scheme with COPE-type NC scheme. We show that Star-NC exploits new coding opportunities different from COPE-type NC and thus can be used with or without this scheme. The results show that Star-NC has often better performance than COPE for a directional traffic model which is a typical model in wireless mesh networks. Moreover, we found that, joint Star and COPE-type NC has better throughput performance than each of Star or COPE alone.








Similar content being viewed by others
References
Ahlswede, R., Cai, N., Li, S.-Y. R., & Yeung, R. W. (2000). Network information flow. IEEE Transactions on Information Theory, 46(1), 1204–1216.
Li, S. Y., Yeung, R. W., & Cai, N. (2003). Linear network coding. IEEE Transaction on Information Theory, 49(2), 371–381.
Li, Z., & Li, B. (2004). Network coding in undirected networks. In Proceedings of the CISS.
Li, Z., & Li, B. (2004). Network coding: The case for multiple unicast sessions. In Proceedings of the Allerton conference on communications.
Wu, Y., Chou, P. A., & Kung, S. Y. (2004). Information exchange in wireless networks with network coding and physical-layer broadcast. MSR-TR-78.
Koetter, R., & Ho, T. (2005). Online incremental network coding for multiple unicasts. In Proceedings of the DIMACS working group on network coding.
Katti, S., Rahul, H., Hu, W., Katabi, D., Medard, M., & Crowcroft, J. (2008). XOR in the air: Practical wireless network coding. IEEE/ACM Transactions on Networking, 16, 497–510.
Sengupta, S., Rayanchu, S., & Banerjee, S. (2007). An analysis of wireless network coding for unicast sessions: The case for coding-aware routing. In Proceedings of the IEEE INFOCOM.
Omiwade, S., Zheng, R., & Hua, C. (Jan. 2008). Butterflies in the mesh: lightweight localized wireless network coding. In Proceedings of NetCod, Lausanne, Switzerland.
Wang, C.-C., & Shroff, N. B. (2010). Pairwise intersession network coding on directed networks. IEEE Transactions on Information Theory, 56(8), 3879–3900.
Yuan, J., Li, Z., Yu, W., & Li, B. (2006). A Cross-layer optimization framework for multihop multicast in wireless mesh networks. IEEE Journal on Selected Areas in Communications, 24(11) 2092–2103.
Zhang, X., & Li, B. (2008). On the benefits of network coding in multi-channel wireless networks. In Proceedings of the IEEE INFOCOM.
Zhang, H., & Su, X. (June 2009). Modeling throughput gain of network coding in multi-channel multi-radio wireless ad hoc networks. International Journal of Selected Area in Communications, 27(5).
Liu, J., Coeckel, D., & Towsley, D. (2007) Bounds on the gain of network coding and broadcasting in wireless networks. In Proceedings of the IEEE INFOCOM.
Gupta, P., & Kumar, P. R. (2000). The capacity of wireless networks. IEEE Transactions on Information Theory, 46(2), 388–404.
Le, J., Lui, J. C. S., & Chiu, D. M. (2008). How many packets can we encode? An analysis of practical wireless network coding. In Proceedings of the IEEE INFOCOM.
Kwon, S., Hendessi, F., & Fekri, F. (2009). Cooperative network coding and coding-aware channel assignment in multi-channel. Multi-interface wireless networks. In Proceedings of the IEEE SECON.
Kwon, S. C., Hendessi, F., Fekri, F., & Stüber, G. L. (Jan 2011). A novel collaboration scheme for multi-channel/interface network coding. IEEE Transactions on Wireless Communications, 10(1), 188–198.
Fragouli, C., Katabi, D., Markopoulou, A., Medard, M., & Rahul, H. (2007). Wireless network coding: Opportunities and challenges. In MILCOM.
De Couto, D. S. J., Aguayo, D., Bicket, J., & Morris, R. (2003). A high-throughput path metric for multi-hop wireless routing. In Proceedings of the ACM MOBICOM (pp. 134–146).
West, D. B. (2001). Introduction to graph theory (2nd ed., pp. 150–170). s.l.: Prentice Hall.
AMPL: A modeling language for mathematical programming. http://www.ampl.com/. (Online) IBM Inc.
CPLEX, ILOG. http://www.ilog.com. (Online) ILOG Inc.
Hassan-Ali, M. (2007). Municipal wireless mesh networks as a comptetive. broadband delivery platform M.S. Thesis, Massachusetts Institute of Technology.
Author information
Authors and Affiliations
Corresponding author
Appendix A: Proof for Theorem 1
Appendix A: Proof for Theorem 1
We explore a sufficient condition for Theorem 1 by proper selection of \(\mathbf{Q}_{{\varvec{M}}}\) and \(\mathbf{Q}_{{\varvec{B}}}\) in which every output nodes is capable of decoding its packet. The output node \(D_{k}\) has a system of \(\eta \) linear equations, out of which \(\eta -m\) of them are received from the relay node’s encoded packets (\(\mathbf{Q}_{{\varvec{M}}})\) and the others are captured by opportunistic listening of neighbor nodes. Therefore, it suffices to show that each output node has enough information to solve its system and decode all of the packets. This condition, for \(k>m\), represents a feature of \(\mathbf{Q}_{{\varvec{M}}} \) in which the deletion of the columns \(i_{k-m} \)through \(i_{k-1} \) results a non-zero determinant matrix. However, for \(k\le m\) this deletion is occurred for the columns \(i_1 \)to \(i_k \) of the union of \(\mathbf{Q}_{{\varvec{M}}}\) and a matrix formed by the first \(m-k\) rows of \(\mathbf{Q}_{{\varvec{B}}}\), and must lead to a non-zero determinant matrix. Next, we use this condition and try to present a constructive proof for Theorem 1 by seeking suitable \(\mathbf{Q}_{{\varvec{M}}}\) and \(\mathbf{Q}_{{\varvec{B}}}\).
Case m \(\mathbf{=1 :}\) Consider \(\mathbf{Q}_{{\varvec{M}}}\) and \(\mathbf{Q}_{{\varvec{B}}}\) matrices as:
For any \(\eta \) (even for \(\eta >3m+2)\), deletion of each column of \(\mathbf{Q}_{{\varvec{M}}}\) produces a non-zero determinant rectangular matrix.
Case m \(\mathbf{=2 :}\) For \(\eta \ge 4\), Consider \(\mathbf{Q}_{{\varvec{M}}}\) as concatenation of the identity matrix of size \(\eta -2\) and a two-columns matrix \(J\), i.e. \(\mathbf{Q}_{{\varvec{M}}} =\left( {\mathbf{I}_{\left( {\eta -2} \right) } \text{| }\mathbf{J}_{\left( {\eta -2} \right) \times 2} } \right) \) where, for different values of \(\eta \), \(J\) is defined as in Table 3. Now, we seek for the pairs of \(\mathbf{Q}_{{\varvec{M}}}\) columns whose deletion produces a zero determinant matrix. This happens in two different cases as either the generation a row of zero elements or remaining a set of linearly dependent columns. Note that, since the first part of \(\mathbf{Q}_{{\varvec{M}}}\) is an identity matrix, it has no linearly dependent rows and thus the deletion a pair of columns (except for \(\eta \) =4) does not leave a matrix with dependent rows. For simple verification, we define tow terms \(ZR(\mathbf{Q}_{{\varvec{M}}})\) and \(CD(\mathbf{Q}_{{\varvec{M}}})\) to denote the sets containing the tuples of the columns of \(\mathbf{Q}_{{\varvec{M}}}\). In the former, each tuple refers to the columns of \(\mathbf{Q}_{{\varvec{M}}}\) whose deletion creates a row of zeros, while in the latter, it refers to the columns whose sum is a zero vector. For \(ZR({\mathbf{Q}}_{{\varvec{M}}})\), we consider in tuples with at most two elements while for \(CD({\mathbf{Q}}_{{\varvec{M}}})\) the tuples with at most \(\eta -2\) elements are concerned. By a little effort, we can compute these sets, shown in Table 3, for the above \(\mathbf{Q}_{{\varvec{M}}}\). Let \(D_\eta ^2 (Q_M )\) denotes a set of column pairs of \(\mathbf{Q}_{{\varvec{M}}}\) whose deletion results a zero determinant matrix. We can write:
Now, we try to find a relation between the ability of decoding for each target permutation and \(D_\eta ^2 (Q_M )\). We define a target permutation as Q\(_\mathrm{M}\)-proper if its first \(\eta -1\) elements do not include any pair of \(D_\eta ^2 (Q_M )\) as two consecutive elements. This condition guaranties the feasibility of decoding for output nodes \(D_3 \) through \(D_\eta \). Obviously, only a subset of the permutations will be Q\(_\mathrm{M}\)-proper. For each the others, we try to exchange the columns of \(\mathbf{Q}_{{\varvec{M}}}\) in a way that it becomes a proper permutation for the altered \(\mathbf{Q}_{{\varvec{M}}}\). The main idea is that we exchange of the columns based on the mapping which converts a non-proper permutation to a proper one. For instance, let \(\rho =\left( {1,2,7,6,8,5,4,3} \right) \) and \(\pi =\left( {6,5,1,2,8,3,7,4} \right) \), it is simple to verify that \(\rho \) is Q\(_\mathrm{M}\)-proper, but \(\pi \) is not. Now, we can create a new matrix \(\acute{\mathbf{Q}}_{M}\) from \(\mathbf{Q}_{{\varvec{M}}}\) by the following exchanges:
Now, \(\pi \) is a \(\acute{\mathbf{Q}}_{{{\varvec{M}}}}\)-proper permutation. We refer to \(\rho \) as generator of \(\pi \). It seems that a single Q\(_\mathrm{M}\)-proper generator, like \(\rho \), is enough for all target permutation. However, we have not verified the ability of decoding for the output nodes \(D_{1}\) and \(D_{2}\) yet. Indeed, these nodes overhear the input nodes \(S_{1}\) and \(S_{2}\) and thus decoding process is further dependent on \(\mathbf{Q}_{{\varvec{B}}}\). We fix our choices of \(\mathbf{Q}_{{\varvec{B}}}\) to an upper triangular matrix with elements of 1 in the main diagonal and all rows expect the second one. This \(\mathbf{Q}_{{\varvec{B}}}\) implies that every input node \(S_{i}\) (\(i\ne 2)\) sends the encoded packet \(\mathop \sum \nolimits _{k=i}^\eta P_k \) to the relay node, i.e., \(S_{i}\) needs to overhear the transmissions of \(S_{i+1}\) and \(S_{i+2}\).
On the other hand, since both \(D_{1}\) and \(D_{2}\) can overhear transmission of \(S_{1}\), i.e., the encoded packet \(\mathop \sum \nolimits _{i=1}^\eta P_i \). In addition to this packet, \(D_{1}\) overhears the native packets \(P_2 \) and \(D_{2}\) overhears \(P_{\pi (1)}\). According to the overheard information, the decoding of \(D_{1}\) and \(D_{2}\) reaches to system of equations whose core is a matrix resulted from \(\mathbf{Q}_{{\varvec{M}}}\) (or \(\acute{\mathbf{Q}}_{{{\varvec{M}}}}\) by adding a row of 1 and deleting the column either 2 (for \(D_{1})\) or \(\pi ({1})\) (for \(D_{1})\). Thus, it is enough to consider the effect of a column deletion in to account either for creation of a row with zero elements or for remaining a set of dependent columns. Since \(ZR(Q_M )\) contains only the tuples of size 2, zeroing a row is not taken by a single column deletion. Further, since the core matrix has a row full of 1, generation a set of dependent column only is occurred for the even tuples of \(CD(Q_M )\). As for \(\eta =4\) and \(\eta =6, CD(Q_M)\) has no even size tuples, the resulting matrices do not have any dependent columns, and hence is suitable for any target permutation. But for \(\eta =5,7\) and 8, the resulting matrices have inherited the even size column dependencies of \(\mathbf{Q}_{{\varvec{M}}}\). Thus, the decoding process could be done if the deletion is occurred for a column among these tuples.
We satisfy this condition by selecting a suitable Q\(_\mathrm{M}\)-proper generator \(\rho \) for each \(\pi \) in a manner that both the columns mapped to \(2\) and \(\pi [1]\) via \(X_{\rho \rightarrow \pi } \), are picked up from these tuples. By selecting \(\rho \) such that \(\rho [1]=1,\) the condition related to column \(\pi [1]\) is met since the first column is appeared in of all the mentioned tuples. The other condition, corresponding to columns 2, is satisfied by choosing a \(\rho \) that the elements of each dependent tuple are located in even positions of \(\rho \) when the position of 2 in \(\pi \) is even and vice versa when the position of 2 in \(\pi \) is odd. Thus, one of the following options is suitable for the generator permutation:
Position of 2 in \(\varvec{\pi } \) | \(\varvec{\eta } =\mathbf{5}\) | \(\varvec{\eta } =\mathbf{7}\) | \(\varvec{\eta } =\mathbf{8}\) |
|---|---|---|---|
odd | \(\left( {\mathbf{1},4,\mathbf{5},3,\mathbf{2}} \right) \) | \((\mathbf{1},3,\mathbf{2},4,\mathbf{6},5,7)\) | \((\mathbf{1},2,\mathbf{3},4,\mathbf{8},6,\mathbf{7},5)\) |
Even | \((1,\mathbf{4},5,\mathbf{2},3)\) | \((1,\mathbf{2},3,\mathbf{6},4,\mathbf{7},5)\) | \((1,\mathbf{2},3,\mathbf{4},6,\mathbf{7},5,\mathbf{8})\) |
Lastly, for \(\text{ m }=3\) and \(\text{ m }=4\), we used an extension of the method for \(\text{ m }=2\) with a subtle difference that the most of verification steps is done by a computerized program. This is due to largeness of state space of the problem. The details of proof are deleted for the lack of space.
Rights and permissions
About this article
Cite this article
Shafieinejad, A., Hendessi, F. & Fekri, F. Star-Structure Network Coding for Multiple Unicast Sessions in Wireless Mesh Networks. Wireless Pers Commun 72, 2185–2214 (2013). https://doi.org/10.1007/s11277-013-1143-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-013-1143-7