Abstract
In cooperative communications, signals are relayed to increase transmission range and user throughput. However, selection and coordination of relay stations (RSs) usually require channel state information (CSI) and control signaling, resulting in high system overhead, latency, and complexity. In this paper, we propose a cooperation scheme for wireless networks, called stochastic cooperative communications based on geometrical probability (SCCGP). SCCGP has a low operational overhead and provides link capacity guarantee statistically. For cellular networks, a base station selects randomly a number of RSs in a hexagonal cell that have a fixed amplification factor, and the target user employs selective combining on the signal copies from multiple relaying paths. For ad hoc networks, the RSs are selected randomly in the circular area between a pair of communicating stations. Using a geometrical probability approach and the Cassini oval model, we derived the distribution functions of the cascaded path loss over a random two-hop relaying path, average received signal-to-noise ratio, and link capacity over multiple relaying paths. Furthermore, we transform the distribution functions into closed forms by using Taylor expansions. The mathematical proof and numerical results have shown that the closed-form distribution functions are valid and can be used to analyze the capacity of SCCGP and determine the minimum number of random RSs needed to satisfy an outage requirement. The SCCGP scheme can improve the user capacity considerably without the need of much coordination and CSI among the RSs. The derived distribution functions of the cascaded path loss over random two-hop paths can also be used in the interference management in multi-source-destination systems and other problems.











Similar content being viewed by others
Notes
The AF relaying scheme is easy to implement in practice compared to the decode and forward (DF) and cooperative coding (CC) schemes.
MRC usually leads to the best performance, but it requires accurate measurements of both the channel gains and phases of all branches. SC has much lower processing complexity.
References
Hazewinkel M (ed) (2001) “Cassini Oval”, encyclopedia of mathematics. Springer Science+Business Media (Kluwer Academic Publishers), Berlin. ISBN 978-1-55608-010-4
Baccelli F, Giovanidis A (2015) A stochastic geometry framework for analyzing pairwise-cooperative cellular networks. IEEE Trans Wireless Commun 14(2):794–808
Biasio D, Cametti C (2005) Effect of the shape of human erythrocytes on the evaluation of the passive electrical properties of the cell membrane. Bioelectrochemistry 65:163–169
Khattabi Y, Matalgah M (2015) Conventional AF cooperative protocol under nodes-mobility and imperfect-CSI impacts: outage probability and shannon capacity. In: Proc. IEEE Wireless communications and networking conference (WCNC). New Orleans, pp 13–18
Liu P, Tao Z, Narayanan S, Korakis T, Panwar S (2007) CoopMAC: a cooperative MAC for wireless LANs. IEEE J Sel Areas Commun 25(2):340–354
Luo Y, Zhang R, Cai L, Xiang S (2014) Finite-state Markov modeling for wireless cooperative networks. IET Netw 3(2):119–128
Qin H, Zhang R, Li B, Cai L (2015) Distributed cooperative MAC for wireless networks based on network coding. In: IEEE Wireless communications and networking conference (WCNC). New Orleans, pp 2050–2055
Shan H, Wang P, Zhuang W, Wan Z (2008) Cross-layer cooperative triple busy tone multiple access for wireless networks. In: Proc. IEEE Global telecommunications conference (GLOBECOM). New Orleans, pp 1–5
Sheng Z, Leung K, Ding Z (2011) Cooperative wireless networks: from radio to network protocol designs. IEEE Commun Mag 49(5):64–69
Song X, Zhang R, Pan J, Liu J (2013) A statistical geometric approach for capacity analysis in two-hop relay communications. In: Proc. IEEE Global telecommunications conference (GLOBECOM). Atlanta, pp 4823–4829
Wang D, Ren P, Du Q, Sun L, Wang Y (2017) Security provisioning for MISO vehicular relay networks via cooperative jamming and signal superposition. IEEE Trans Veh Technol 66(12):10732–10747
Wang D, Ren P, Chen J (2018) Cooperative secure communication in two-hop buffer-aided networks. IEEE Trans Commun 66(3):972–985
Wang X, Liang Q (2013) On the ergodic capacity of cooperative-diversity networks with decode-and-forward relaying over nakagami-m fading channels. In: Proc. IEEE Global telecommunications conference (GLOBECOM). Atlanta, pp 3832– 3837
Zhang R, Ban D, Li B, Jiang Y (2016) The cooperative multicasting based on random network coding in wireless networks. In: Proc. IEEE Vehicular technology conference (VTC-Spring). Nanjing, pp 1–5
Zhuang W, Zhou Y (2013) A survey of cooperative MAC protocols for mobile communication networks. J Internet Technol 14(4):541–559
Acknowledgements
This work was supported in part by the National Natural Science Foundation of China (61571370, 61601365, and 61801388) and in part by the China Postdoctoral Science Foundation (BX20180262, 2018M641019, and 2018M641020).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix: Validation of the elliptic integrals
Appendix: Validation of the elliptic integrals
The Elliptic Integrals of the second kind in (11a) is
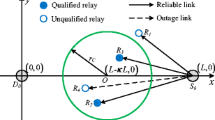
where \(X_{\beta _{A}} = \frac {a^{4}}{d^{2}}\sin ^{2}\theta \) is defined for easy presentation. From Fig. 3 and trigonometry, we can get
Then \(X_{\beta _{A}}\) becomes (36).
According to Fig. 3, the phase of the intersection point, βA, is in the range of \(\beta _{A} \in \left [0,\ \frac {\pi }{2}\right ]\). The range of the integral variable 𝜃 in (34) is \(\theta \in \left [0,\ 2\beta _{A} \right ]\). When \(\beta _{A} \leq \frac {\pi }{4}\), \(X_{\beta _{A}}\) is maximized at 𝜃 = 2βA. When \(\beta _{A} > \frac {\pi }{4}\), \(X_{\beta _{A}}\) is maximized at \(\theta = \frac {\pi }{2}\). Therefore, given βA, the maximum of \(X_{\beta _{A}}\) is in (37).
It can be observed from (37) that when \(\beta _{A} = \frac {\pi }{4}\), \(\max \left \{X_{\beta _{A}}\right \}\) achieves the maximum. Therefore, by plugging \(\beta _{A} = \frac {\pi }{4}\) into (37), we can get (38).
Since \(X_{\beta _{A}}\) is bounded by 0.49, the Elliptic Integral in (11a) is valid.
Similarly, the Elliptic Integral of the second kind in the CDF in (11b) is
where the 𝜃 is in the range of \(\theta \in \left [0,\ \pi \right ]\). Because this integral exists in the CDF under the condition of \(\sqrt {d}>a\), the item \(X_{\beta _{A}} = \frac {a^{4}}{d^{2}}\sin ^{2}\theta \) is maximized when \(\theta = \frac {\pi }{2}\) and \(d \rightarrow a^{2}\). Thus, we can obtain \(\max \left \{X_{\beta _{A}}\right \} \rightarrow 1\). Since \(X_{\beta _{A}}\) is bounded by 1, the Elliptic Integral in (11b) is validated.
Rights and permissions
About this article
Cite this article
Zhang, R., Song, X., Pan, J. et al. Stochastic Cooperative Communications Using a Geometrical Probability Approach for Wireless Networks. Mobile Netw Appl 24, 1437–1451 (2019). https://doi.org/10.1007/s11036-019-01266-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-019-01266-y