Abstract
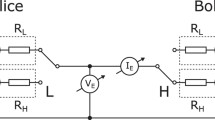
We classify and analyze bit errors in the current measurement mode of the Kirchhoff-law–Johnson-noise (KLJN) key distribution. The error probability decays exponentially with increasing bit exchange period and fixed bandwidth, which is similar to the error probability decay in the voltage measurement mode. We also analyze the combination of voltage and current modes for error removal. In this combination method, the error probability is still an exponential function that decays with the duration of the bit exchange period, but it has superior fidelity to the former schemes.





Similar content being viewed by others
References
Liang, Y., Poor, H.V., Shamai, S.: Information theoretic security. Found. Trends Commun. Inf. Theory 5, 355–580 (2008). doi:10.1561/0100000036
Bennett, C.H., Brassard, G., Breidbart, S., Wiesner, S.: Quantum cryptography, or unforgeable subway tokens. In: Advances in Cryptology: Proceedings of Crypto ’82, pp. 267–275. Plenum Press, Santa Barbara (1982)
Yuen, H.P.: On the foundations of quantum key distribution—reply to Renner and beyond (2012). arXiv:1210.2804
Yuen, H.P.: Unconditional security in quantum key distributions (2012). arXiv:1205.5065v2
Hirota, O.: Incompleteness and limit of quantum key distribution theory (2012). arXiv:1208.2106v2
Renner, R.: Reply to recent skepticism about the foundations of quantum cryptography (2012). arXiv:1209.2423v1
Yuen, H.P.: Security significance of the trace distance criterion in quantum key distribution (2012). arXiv:1109.2675v3
Merali, Z.: Hackers blind quantum cryptographers. Nat. News (2009). doi:10.1038/news.2010.436
Gerhardt, I., Liu, Q., Lamas-Linares, A., Skaar, J., Kurtsiefer, C., Makarov, V.: Full-field implementation of a perfect eavesdropper on a quantum cryptography system. Nat. Commun. 2, 349 (2011). doi:10.1038/ncomms1348
Lydersen, L., Wiechers, C., Wittmann, C., Elser, D., Skaar, J., Makarov, V.: Hacking commercial quantum cryptography systems by tailored bright illumination. Nat. Photonics 4, 686–689 (2010). doi:10.1038/NPHOTON.2010.214
Gerhardt, I., Liu, Q., Lamas-Linares, A., Skaar, J., Scarani, V., Makarov, V., Kurtsiefer, C.: Experimentally faking the violation of Bell’s inequalities. Phys. Rev. Lett. 107, 170404 (2011). doi:10.1103/PhysRevLett.107.170404
Makarov, V., Skaar, J.: Faked states attack using detector efficiency mismatch on SARG04, phasetime, DPSK, and Ekert protocols. Quantum Inf. Comput. 8, 622–635 (2008)
Wiechers, C., Lydersen, L., Wittmann, C., Elser, D., Skaar, J., Marquardt, C., Makarov, V., Leuchs, G.: After-gate attack on a quantum cryptosystem. New J. Phys. 13, 013043 (2011). doi:10.1088/1367-2630/13/1/013043
Lydersen, L., Wiechers, C., Wittmann, C., Elser, D., Skaar, J., Makarov, V.: Thermal blinding of gated detectors in quantum cryptography. Opt. Express 18, 27938–27954 (2010). doi:10.1364/OE.18.027938
Jain, N., Wittmann, C., Lydersen, L., Wiechers, C., Elser, D., Marquardt, C., Makarov, V., Leuchs, G.: Device calibration impacts security of quantum key distribution. Phys. Rev. Lett. 107, 110501 (2011). doi:10.1103/PhysRevLett.107.110501
Lydersen, L., Skaar, J., Makarov, V.: Tailored bright illumination attack on distributed-phase-reference protocols. J. Mod. Opt. 58, 680–685 (2011). doi:10.1080/09500340.2011.565889
Lydersen, L., Akhlaghi, M.K., Majedi, A.H., Skaar, J., Makarov, V.: Controlling a superconducting nanowire single-photon detector using tailored bright illumination. New J. Phys. 13, 113042 (2011). doi:10.1088/1367-2630/13/11/113042
Lydersen, L., Makarov, V., Skaar, J.: Comment on “Resilience of gated avalanche photodiodes against bright illumination attacks in quantum cryptography”. Appl. Phys. Lett. 99, 196101 (2011). doi:10.1063/1.3658806
Sauge, S., Lydersen, L., Anisimov, A., Skaar, J., Makarov, V.: Controlling an actively-quenched single photon detector with bright light. Opt. Express 19, 23590–23600 (2011). doi:10.1364/OE.19.023590
Lydersen, L., Jain, N., Wittmann, C., Maroy, O., Skaar, J., Marquardt, C., Makarov, V., Leuchs, G.: Superlinear threshold detectors in quantum cryptography. Phys. Rev. Lett. 84, 032320 (2011). doi:10.1103/PhysRevA.84.032320
Lydersen, L., Wiechers, C., Wittmann, C., Elser, D., Skaar, J., Makarov, V.: Avoiding the blinding attack in QKD: reply (comment). Nat. Photonics 4, 800–801 (2010). doi:10.1038/nphoton.2010.278
Makarov, V.: Controlling passively quenched single photon detectors by bright light. New J. Phys. 11, 065003 (2009). doi:10.1088/1367-2630/11/6/065003
Yuen, H.P.: Key generation: foundation and a new quantum approach. IEEE J. Sel. Top. Quantum Electron. 15, 1630–1645 (2009). doi:10.1109/JSTQE.2009.2025698
Salih, H., Li, Z.H., Al-Amri, M., Zubairy, H.: Protocol for direct counterfactual quantum communication. Phys. Rev. Lett. 101, 170502 (2013). doi:10.1103/PhysRevLett.110.170502
Kish, L.B.: Totally secure classical communication utilizing Johnson (-like) noise and Kirchhoff’s law. Phys. Lett. A 352, 178–182 (2006). doi:10.1016/j.physleta.2005.11.062
Mingesz, R., Kish, L.B., Gingl, Z., Granqvist, C.G., Wen, H., Peper, F., Eubanks, T., Schmera, G.: Unconditional security by the laws of classical physics. Metrol. Meas. Syst. 20, 3–16 (2013). doi:10.2478/mms-2013-0001
Kish, L.B., Abbott, D., Granqvist, C.G.: Critical analysis of the Bennett–Riedel attack on secure cryptographic key distributions via the Kirchhoff-law–Johnson-noise scheme (2013). arXiv:1306.0058
Kish, L.B.: Protection against the man in the middle attack for the Kirchhoff-loop Johnson (-like) -noise cipher and expansion by voltage-based security. Fluct. Noise Lett. 6, L57–L63 (2005). doi:10.1142/S0219477506003148
Kish, L.B.: Enhanced secure key exchange systems based on the Johnson noise scheme. Metrol. Meas. Syst. 20, 191–204 (2013). doi:10.2478/mms-2013-0017
Mingesz, R., Gingl, Z., Kish, L.B.: Johnson (-like) -noise–Kirchhoff-loop based secure classical communicator characteristics, for ranges of two to two thousand kilometers, via model-line. Phys. Lett. A 372, 978–984 (2008). doi:10.1016/j.physleta.2007.07.086
Saez, Y., Kish, L.B.: Errors and their mitigation at the Kirchhoff-law–Johnson-noise secure key exchange (2013). arXiv:1305.0126; arXiv:1305.4787v1
Kish, L.B., Kwan, C.: Physical uncloneable function hardware keys utilizing Kirchhoff-law–Johnson-noise secure key exchange and noise-based logic (2013). arXiv:1305.0068; arXiv:1305.3248
Kish, L.B., Saidi, O.: Unconditionally secure computers, algorithms and hardware. Fluct. Noise Lett. 8, L95–L98 (2008). doi:10.1142/S0219477508004362
Gonzalez, E., Kish, L.B., Balog, R., Enjeti, P.: Information theoretically secure, enhanced Johnson noise based key distribution over the smart grid with switched filters. PLoS ONE 8, e70206 (2013). doi:10.1371/journal.pone.0070206
Kish, L.B., Mingesz, R.: Totally secure classical networks with multipoint telecloning (teleportation) of classical bits through loops with Johnson-like noise. Fluct. Noise Lett. 6, C9–C21 (2006). doi:10.1142/S021947750600332X
Kish, L.B., Peper, F.: Information networks secured by the laws of physics. IEICE Trans. Commun. 95-B, 1501–1507 (2012)
Kish, L.B., Mingesz, R., Gingl, Z., Granqvist, C.G.: Spectra for the product of Gaussian noises. Metrol. Meas. Syst. 19, 653–658 (2012). doi:10.2478/v10178-012-0057-0
Rice, S.O.: Mathematical analysis of random noise. Bell Syst. Tech. J. 23, 282–332 (1944). http://archive.org/details/bstj23-3-282
Rychlik, I.: On some reliability applications of Rice’s formula for the intensity of level crossings. Extremes 3, 331–348 (2000). doi:10.1023/A:1017942408501
Acknowledgements
Discussions with Elias Gonzalez are appreciated. Y. Saez is grateful to IFARHU/SENACYT for supporting her PhD studies at Texas A&M. R. Mingesz’s contribution is supported by the European Union and the European Social Fund. Project #TÁMOP-4.2.2.A-11/1/KONV-2012-0073.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Saez, Y., Kish, L.B., Mingesz, R. et al. Current and voltage based bit errors and their combined mitigation for the Kirchhoff-law–Johnson-noise secure key exchange. J Comput Electron 13, 271–277 (2014). https://doi.org/10.1007/s10825-013-0515-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10825-013-0515-2